AdLoad
 AdLoad es una herramienta maliciosa destinada a infiltrar adware potencialmente molesto en su sistema basado en Mac. La herramienta ha estado en circulación durante casi tres años y no muestra signos de desaceleración. Su larga permanencia se debe a su capacidad para evolucionar lo suficientemente rápido como para evitar ser detectado. A lo largo de su evolución, AdLoad supuestamente ha eliminado docenas de aplicaciones potencialmente no deseadas (PUA): Kreberisec, SearchDaemon, DataSearch, ApolloSearch, AphroditeResults y muchas otras (consulte la lista a continuación) en un sinnúmero de sistemas MacOS en todo el mundo. Teniendo en cuenta la naturaleza de esas aplicaciones, AdLoad no se comporta como una amenaza típica de nivel severo. Sin embargo, su comportamiento persistente convierte cualquier intento de eliminación en una tarea bastante desafiante.
AdLoad es una herramienta maliciosa destinada a infiltrar adware potencialmente molesto en su sistema basado en Mac. La herramienta ha estado en circulación durante casi tres años y no muestra signos de desaceleración. Su larga permanencia se debe a su capacidad para evolucionar lo suficientemente rápido como para evitar ser detectado. A lo largo de su evolución, AdLoad supuestamente ha eliminado docenas de aplicaciones potencialmente no deseadas (PUA): Kreberisec, SearchDaemon, DataSearch, ApolloSearch, AphroditeResults y muchas otras (consulte la lista a continuación) en un sinnúmero de sistemas MacOS en todo el mundo. Teniendo en cuenta la naturaleza de esas aplicaciones, AdLoad no se comporta como una amenaza típica de nivel severo. Sin embargo, su comportamiento persistente convierte cualquier intento de eliminación en una tarea bastante desafiante.
Tabla de contenido
¿Un secuestrador o un troyano?
AdLoad parece tener una naturaleza dudosa. Por un lado, comparte los rasgos típicos de los secuestradores de navegadores clásicos. Viene disfrazado como una actualización de software falsa o como una descarga automática. Por otro lado, algunos investigadores tienden a clasificar AdLoad como una entidad similar a un troyano debido a su funcionalidad de puerta trasera para colocar todo tipo de aplicaciones no deseadas en un sistema host Mac.
Una vez dentro, AdLoad redirige la actividad de navegación web de las víctimas a servidores predeterminados mediante ataques man-in-the-middle. Estos redireccionamientos generalmente ocurren cuando los actores a cargo quieren monetizar los ingresos publicitarios al redirigir a los usuarios de computadoras a sitios infestados de anuncios de pago por clic (PPC). Si bien este modelo publicitario no es de ninguna manera perjudicial cuando se aplica con los motores de búsqueda más populares en la Web, puede causar problemas si se explota por razones equivocadas. Esto último generalmente involucra a anunciantes que pagan a motores de búsqueda menos conocidos para dirigir tráfico a sitios web con muchos PPC de naturaleza no demasiado sabrosa.
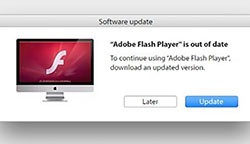
La propagación de AdLoad puede tener lugar durante la carga de aplicaciones empaquetadas o software gratuito. Puede haber casos de instalación de AdLoad a través de las indicaciones de Flash Player, como se ve en la imagen a continuación. A menudo, un aviso de instalación de Flash Player es un sitio web que ha cargado un script o una página que intenta engañar a los usuarios de computadoras para que descarguen e instalen los archivos asociados con AdLoad, lo que permite la instalación de AdLoad donde luego puede bombardear a los usuarios de computadoras Mac con mensajes emergentes. hasta anuncios.

Ejemplo de solicitud de instalación de AdLoad a través de un mensaje de instalación de Flash Player.
A pesar de la longevidad de AdLoad, sigue siendo difícil de detectar hasta el día de hoy, como se muestra en VirusTotal, ya que el adware coloca varios archivos en una gran cantidad de directorios. La mayoría de los datos caen en varias carpetas de la sección Biblioteca local. Luego, ejecuta uno o más ejecutables, que establecen una conexión de escritorio remoto a través de un script de Python. Además de las carpetas visibles en la sección Biblioteca local, AdLoad puede crear una carpeta oculta diseñada para mantener el adware en ejecución.
Indicadores de una infección de AdLoad
Como cualquier otra pieza de adware, AdLoad puede ralentizar su sistema, traerle innumerables anuncios y llevarlo a sitios web que quizás nunca haya visto antes. Los anuncios pueden ofrecer actualizaciones de software falsas, descargas automáticas, bienes y servicios atractivos. Sin embargo, tenga cuidado con este último. Especialmente si se ven demasiado bien para ser verdad.
PUA asociadas
AdLoad supuestamente ha traído docenas de aplicaciones no deseadas a computadoras específicas basadas en MacOS. Algunas de esas aplicaciones no deseadas incluyen, entre otras: WebSearchStride, TotalAdviseSearch, Sorimbrsec, SkilledProjectSearch, SearchRange, SearchNetCharacter, PositiveSearch, KeyWordsSearch, MajorChannelSearch, AlphaLookup, GoldResults, GlobalQuestSearch, LeadingSignSearch, Upgrade, OdysseusLool, Results NetToolboxSearch, SimpleFunctionSearch, AresLookup, PublicAdviseSearch, MajorLetterSearch, SearchArchive, SearchRange, CalypsoLookup, BinarySignSearch, etc.
La lista anterior es sólo una muestra de AdLoad Adware es capaz de traer a la mesa. Si uno o más de estos nombres le suenan, es probable que tenga una infección de AdLoad en curso y deba tomar medidas.
Consejos de eliminación
Para empezar, puede seguir el procedimiento de eliminación convencional llevando a la Papelera las aplicaciones sospechosas o desconocidas que encuentre en su carpeta de Aplicaciones. Luego, puede limpiar cualquier archivo AdLoad residual que encuentre en su biblioteca. Preste especial atención a la carpeta LaunchAgents en particular. Sin embargo, no olvide revisar todas las carpetas de la biblioteca. Si bien estos pasos pueden funcionar, escanear su sistema con una solución antimalware de buena reputación no le hará daño. Recomendamos encarecidamente que haga lo último, ya que AdLoad ha demostrado ser persistente más allá de toda medida cuando es atacado.

